Try Hack Me - HackPark
 A box where brute force meets logical intrusion
A box where brute force meets logical intrusion
Welcome back to my blog, its been a few days since I last did one of these. Catching up, I have begun my adventure on the offensive pentesting course from THM. These starting boxes have been a struggle, I’m talking 4-8 hrs per box on average. Now, with a little perservence I’ve been getting them done slowly but surely.
NOTE: view page source for the answers
This box starts off with a common login page:
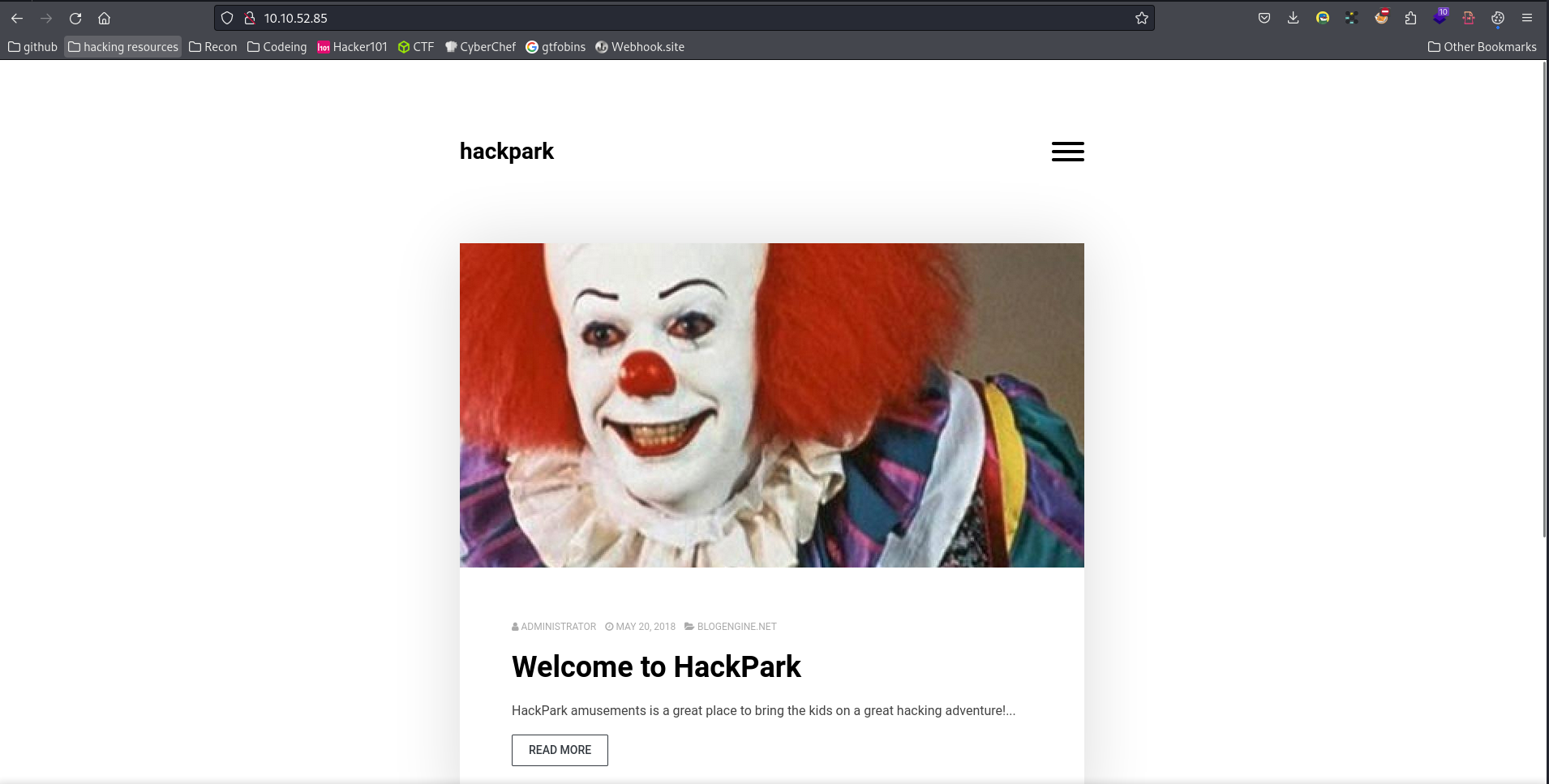
Using Hydra to brute-force a login
I start off with a reverse image search of the image to get the first question:
“What is the name of the clown?”
Moving on, we can look within the networking tab to get the answer for the next question:
“What request type is the Windows website login form using?”
A simple brute force on the page using hydra and the username admin gets us the third question: “Guess a username, choose a password wordlist and gain credentials to a user account!” Note:
- The hydra request will look a little something like this (I used rockyou.txt located in /usr/share/wordlists)
hydra -l <username> -P .<password list> $ip -V http-form-post '/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log In&testcookie=1:S=Location'
Compromising the machine
After logging into the page we are presented with this:
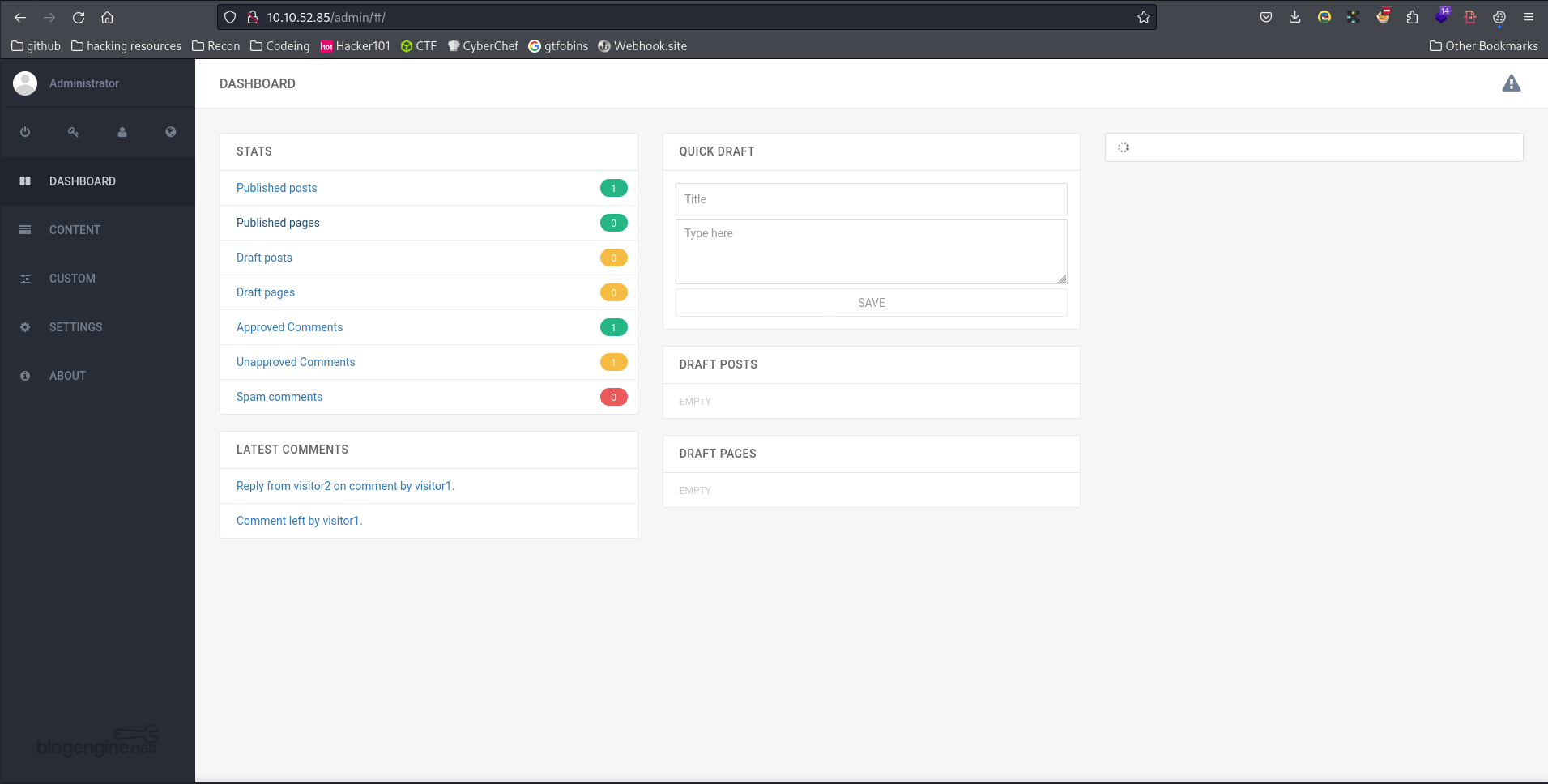
Going to the about section of the page finds us the next question answer:
“Now you have logged into the website, are you able to identify the version of the BlogEngine?”
Finding and exploiting the CVE for the next question wasn’t as hard as I thought it would be. Reading the description of the exploit we see that we need to upload the file to the server (modifying the file with our ip/port of course)
The link that allows us to upload to the server is:
http://10.10.10.10/admin/app/editor/editpost.cshtml
Now, once the file is on the server we start up a nc listener with:
nc -lvnp <port>
And then send a request to:
http://10.10.10.10/?theme=../../App_Data/files
This will effectively execute the payload and give us our first shell
Exploiting that CVE we can run whoami to find out the user we logged in as
Meterpreter
After gaining initial access its always a good idea to establish a meterpreter shell for ease of access. In order to do this we make a msfvenom payload and upload it to the already established netcat session we have on the machine. We start up the msfconsole and enter the same information we entered for the msfvenom payload. Moving the msfvenom exe into the pennywise box and executing us gives us the meterpreter shell.
Windows Privilege Escalation
The next question asks us what the os version is. We can find that by entering systeminfo.
Now, personally I used winpeas because the exploit suggester that the creator had mentioned was very outdated. Booting up winpeas onto the machine and looking at the output we can see this: (Also this is the question to the next answer)
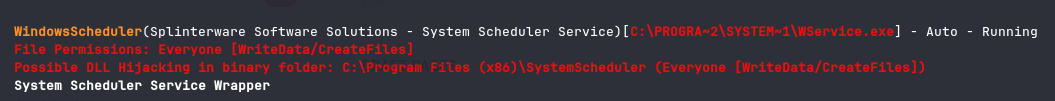
Anyways, going to this directory and viewing the log files we can see:
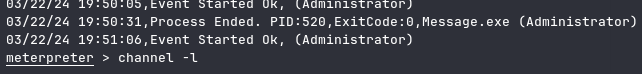
From this log entry we can deduce that Message.exe is one of the processes we
should look out for. And, this process is restarted every 35 seconds. Knowing
this and that everyone can write to the directory it is stored in provides us
with a great exploit opportunity.
We can exploit this vuln by creating a payload named Message.exe and waiting to curl where the original Message.exe is stored. Waiting till our clock reads past 31 seconds we can send the curl request with the message.exe and it will be auto executed when the service comes back up. Just like that you have full pwned the box. ![]()
Privilege Escalation no Metasploit
So, I think here I kind of cheated.. apparenly you weren’t supposed to use winpeas for the initial finding of the exploit. However, I did. So, as you probably can guess this part we already have solved. Feel free to check the page source for the answers. ![]()
And with that this box is completed!
What I learned from this box
- Nothing

Just kidding, I had never used winpeas before so it was really nice to have a change in OS to better my understandings. And I learned that sometimes with wrong file permissions and a task scheduler it can lead to unwanted privilege escalation.
