Try Hack Me - Internal
 About this box: XML-RPC exploit finds a match with easy credentials
About this box: XML-RPC exploit finds a match with easy credentials ![]()
Note: answers in comments
Info
Screenshot of the briefing if interested
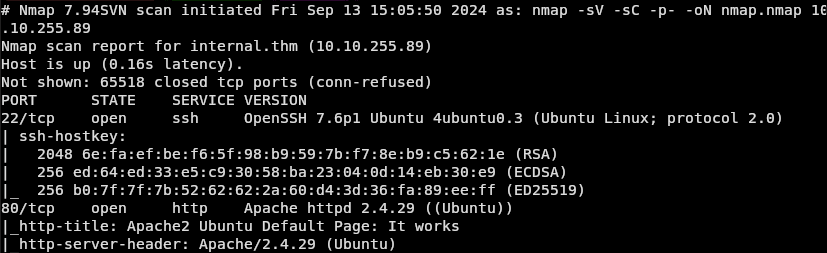
Nmap:
The Beginning
We begin this box with a default apache2 welcome screen. This screen doesn’t mean too much to us so we look around the machine a little more.
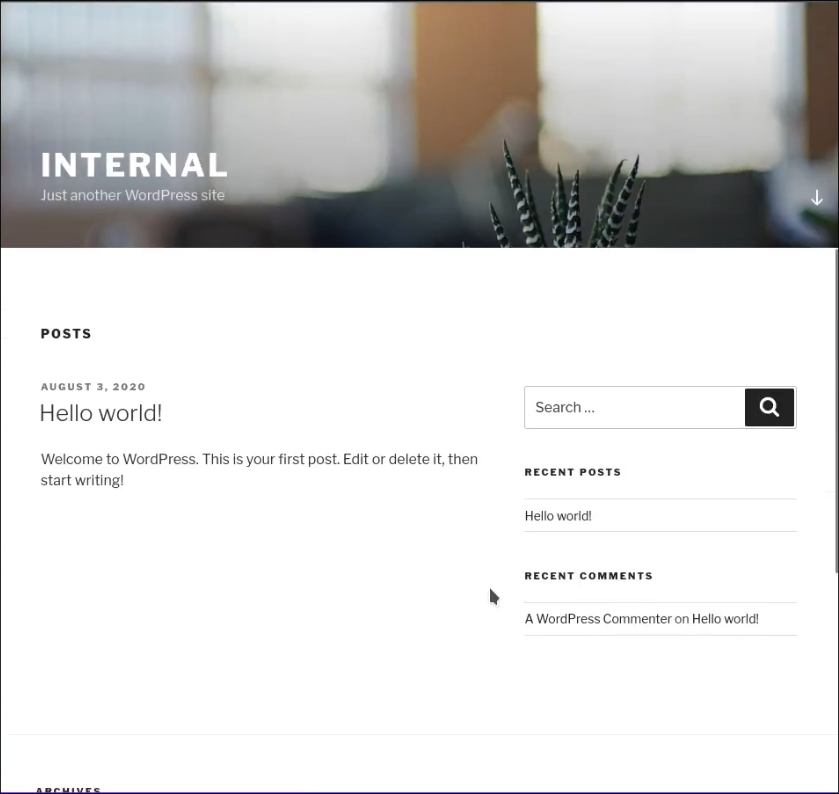
Wordpress
Upon further inspection we see that there is a /blog section running wordpress 5.4.2.
This
blog tells us that navigating to https://gosecure.ai/blog/2021/03/16/6-ways-to-enumerate-wordpress-users/ we can see the users on the machine.
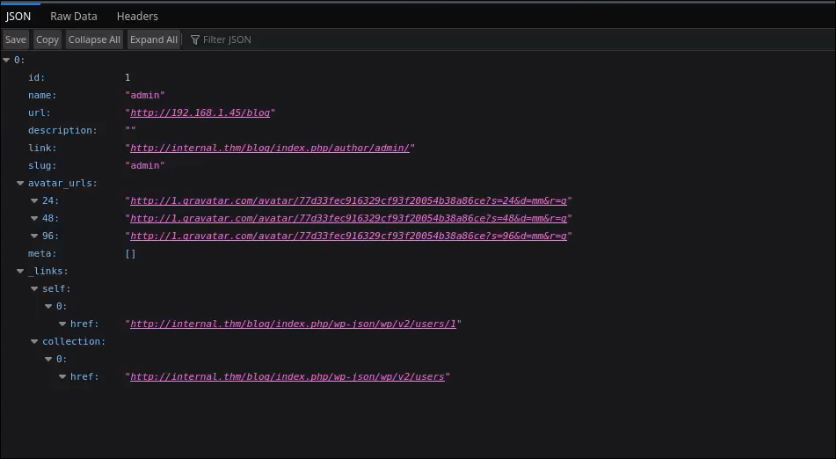
We now have the user admin for the wordpress login page.
There is a tool called wpscanner that allows us to find exploits and misconfigurations on the word press server.
Running wpscan on the server using the --url to point to the /blog endpoint we see this in the results:
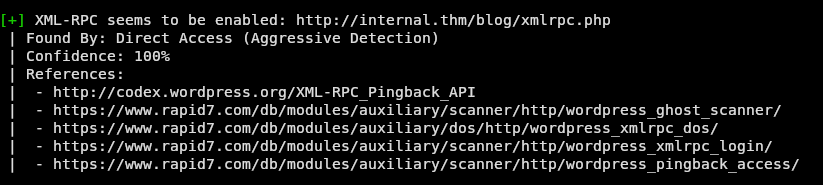
Looking further into this we see that this allows us to make multiple password requests with one http request. Now what does this mean exactly? You are able to guess thousands of passwords with one request by sending a post to a specific endpoint that will check if you have authentication.
In this case we don’t have to worry about the payload since wpscan takes care of it with the following:
wpscan -e vp vt -U admin -P rockyou.txt --url http://internal.thm/blog/
- -e (vulnerablity flags)
- -U (username)
- -P (password file)
- –url (ofc the target)
We get back the results:
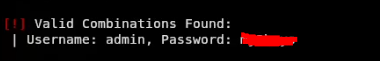
Time to LOGIN! ![]()
Upon logging in we see that we have full access to the wp dashboard. In this case word press contains PHP scripts that handle the page’s theme behavior. What else can be made in PHP?
Reverse shell!
Reverse Shell
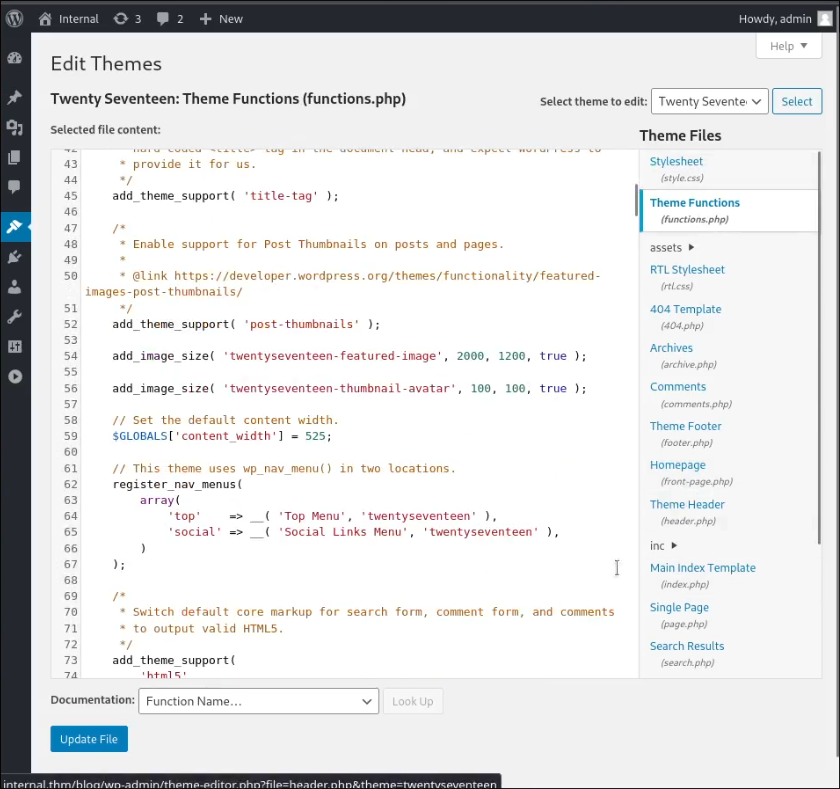
I happened to use the traditional pentest monkey shell found here. (Make sure to change the ip and port)
Setting up a nc listener with nc -lvnp 8000, we can now browse to the main
blog page (seeing that this will reload the config). And just like that we have
a shell on the user www-data.
www-data user
This user is nothing special. No perms, no fun. I spent a lot of time looking through website configs, scanning linpeas output, and more. Nothing… Wait, whats in the /opt directory?
A file named wp-save.txt?
cat wp-save.txt == THE PASSWORD FOR AUBREANNA!?!?!
Now with the new found credentials we ssh into the machine.
Aubreanna
Upon entering the machine we are greeted with the user flag, docker directory, and jenkins.txt.
Submitting the flag, and outputting the jenkins.txt it reads:
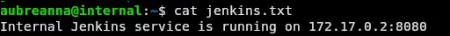
Now how could this be useful… ![]()
Ssh has a feature with the flag -L that allows us to port forward ports (allowing a external user not on the current machine) to have access to the otherwise blocked off service.
This command looks something like this:
ssh -L 9999:172.17.0.2:8080 aubreanna@internal.thm
- -L - creates a listner
- 9999 - the port we forward to (for our machine)
- 8080 - port we want to forward to our machine on 9999
- ssh user credentials for login
Jenkins
Now, navigating to http://localhost:9999 we see this page:
Here, we assume that the user is admin on the machine. This is due to there not being a way to check the version of jenkins running. (That I could find)
Time to run another brute force ![]()
Hydra gives us the credentials to admin RAHH!
Logging in, we navigate to the groovy tab (per usual) and run a handy dandy reverse shell. You can find the one I used here.
Note: if you are doing this yourself change the ip/port/and set cmd=/bin/bash. Run nc -lvnp port and execute the command in the groovy console.
Jenkins User
The last users credentials were in /opt, so this is where I go to first.
Whats this? More credentials?!?!?
Sshing in to the box with the new root credentials will give you the final flag.
![]() Box PWNED
Box PWNED ![]()
What I learned from this box
- Jenkins shell
- To take my time and look through basic directories
- wordpress enumeration
- Linux user enumeration
– Ryu out
