Try Hack Me - Relevant
 About this box: A windows NT machine with the MS17-010 EternalRomance
vulnerability.
About this box: A windows NT machine with the MS17-010 EternalRomance
vulnerability.
Info
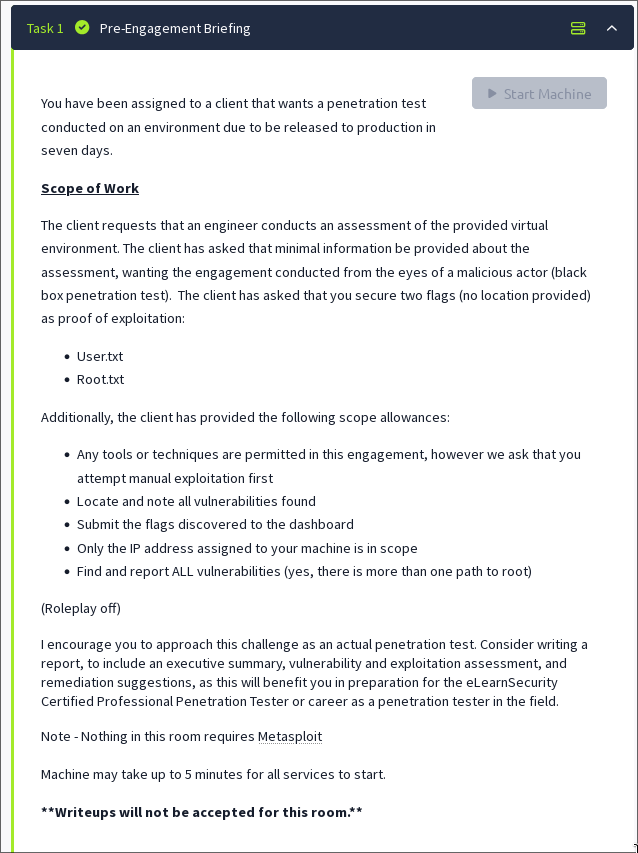
Within Try Hack Me, looking at the specifications of this box, the creator mentions to enter this box as if a black box pentest.
So, What do I do? Just that ![]()
Screenshot of the briefing if interested
The Beginning
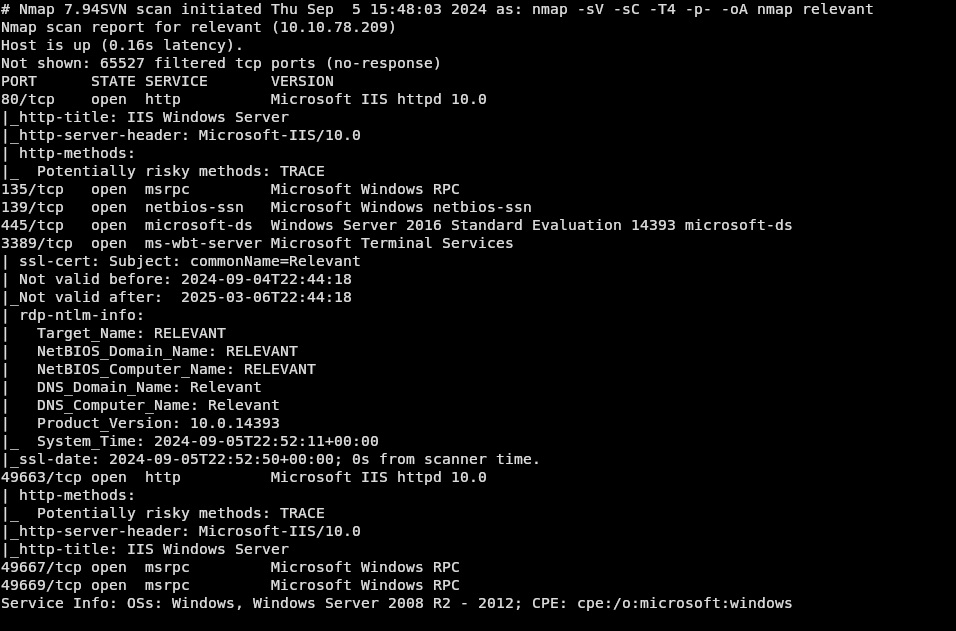
This box started off with a normal nmap scan:
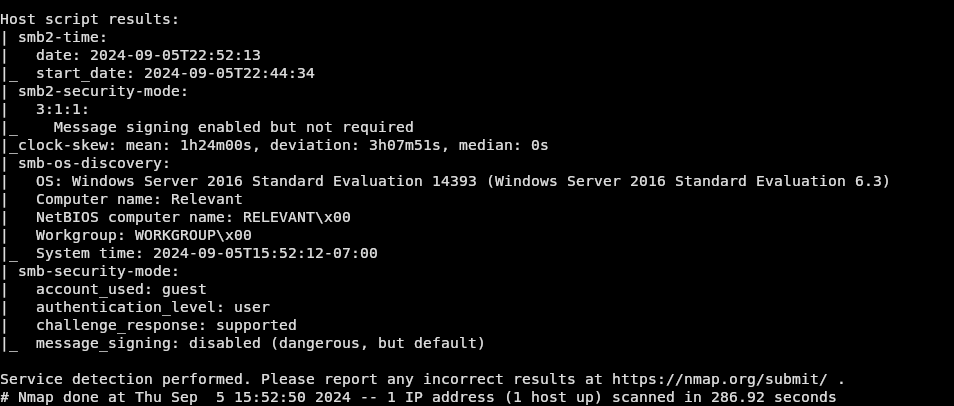
as well as the advanced nmap scan:
I see that there is the opportunity for a MS web server, so I plug the machines ip into the browser to find…
Nothing ![]()
Looking a little deeper into the Nmap scan I see that there is a SMB share. I haven’t dabbled too much in shares, so I turn to google. After a little research I find out that you can enumerate smb shares with:
smbclient -L //ip/ -U user
Now for a user…
Reading more of the -sC portion of the nmap scan it tells us that there is a guest user on the SMB share.
BOOM! ![]()
Now we can do the SMB enumeration. Running the command now with the guest user:
smbclient -L //ip/ -U guest
We get a password prompt ![]()
Wait! SMB by default doesnt have a guest password, hitting enter does the trick in this case (no input).
SMB share list:
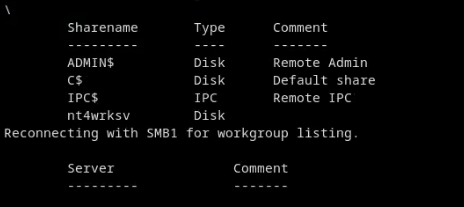
We see a weird share named nt4wrksv. Looking within this share there is a passwords.txt file. Odd I know….
Downloading the file with mget will give us two base64 encoded strings. Putting these into cyberchef (shoutout them, base64 -d in terminal is very inconsistant for me), I get the credentials:
- Bob - !P@$$W0rD!123
- Bill - J#m$dRfM4@20969696$!
Now the next challenge, what to do with these credentials. ![]()
We know there is a rdp server, so lets try that! I boot up the rdp client for linux and put in the credentials with Relevant as the domain. Andddd, no connection. Bummer
At this point in time I think this machine is vulnerable to the MS17-10 Eternal Blue exploit. (I got the idea after running nmap --script vuln ip).
After running countless exploit trials, and attempting to modify my own exploit I decided to move onto another potential way to enter the machine. This so happened to be the other exploit named MS17-10 Eternal Romance.
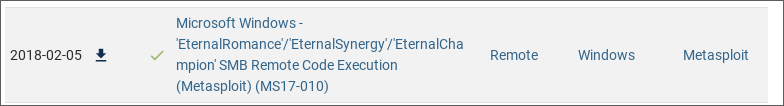
Putting this exploit into msfconsole, I then change the exit function to process, and set the other options accordinly (using Bob and his password as the credentials).
Just like that were in!
Running a simple whoami will tell us that we are NT-AUTHORITY\SYSTEM. What is this user? According to
this site
it tells us that our current user is admin ![]()
Seems too simple?
It was, however according to the author there are plenty of other ways to pwn this box. My plan is to go back and find more places that are vulnerable. Also, running windows exploit suggester showed that there were over 700 vulnerabilities present on the machine. So, time to go hunt more!
P.S. Since you have admin, running a simple find command for .txt’s will give you the user/admin flag
What I learned from this box
- SMB Shares
- Windows host enumeration
- That exploits can have VERY similar names
- How to use linux RDP client
